Knowledge Base Guide [Advanced] - Dedicated VPN server into main network with seperate router
If you manage a number of remote sites, and have complicated access rules between the vlans at each remote sites and your main site, you can quickly run out of useable IP Groups and IP-Port Groups, as well as Gateway and Switch ACL rule counts on your main site to control it. It also becomes messy and very complicated.
This guide will show you how to move this onto a separate gateway, acting as a VPN "Hub" for all remote sites and dial-in clients, and connecting directly into your main network.
In my example, my main site is an ER8411, and my VPN server is an ER7206 v2
Prerequisites
You need at least 2 public IPs on your main site, as we will locate the VPN server here
Omada Controller
Omada Switches
2 Omada Gateways
Step 1
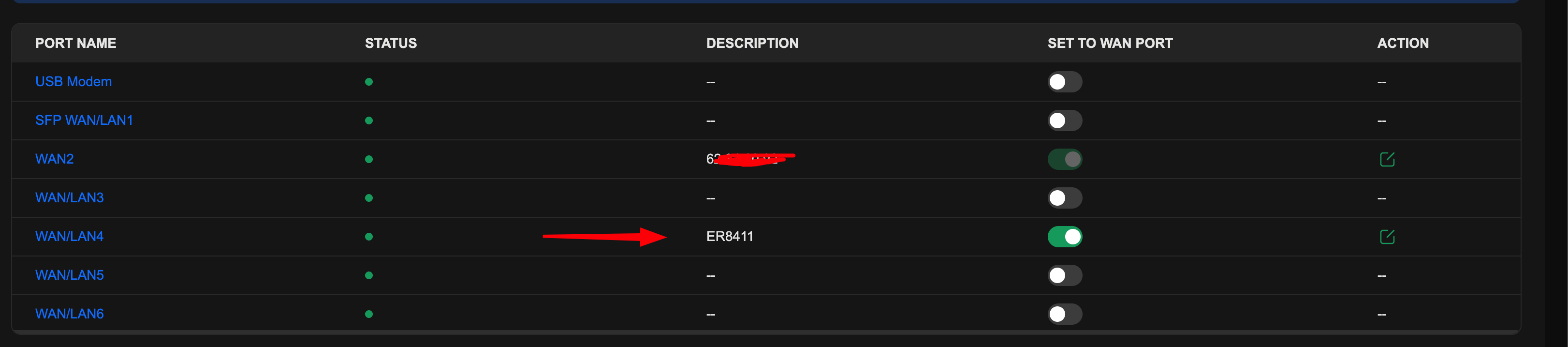
Setup a dedicated WAN port on your main gateway with an IP address outside the scope of any that you use on your LANs
Here, i set up WAN/LAN6 as my dedicated Inter-gateway WAN link on my 8411
Give it an IP and a subnet, you dont need to set DNS or Gateway
In my case, the wan IP is 10.254.254.253, the WAN IP of the ER7206 we set up later will be 10.254.254.254
![]()

STEP 2
Now, set up port forwarding from the WAN IP of what we wil set the ER7206 (.254) to the Omada controller on your LAN

STEP 3
(sorry, no screen shots)
Factory reset your VPN server gateway (ER7206 in my case), and disconnect it from everything except a computer to do the initial configuration. When it is booted, log into its standalone GUI. Set the controller IP/Inform URL to 10.254.254.253 (WAN ip of ER8411). Enable a 2nd WAN port on it (we will need two!). It will reboot after enabling the second WAN port. When its rebooted, log in again and set up the 2nd WAN port you enabled with the following IP (using my example) 10.254.254.254 / 255.255.255.0
Now, reboot it again and set it aside
STEP 4
Set up a new Omada site, configure the WAN to match your gateway model, ensuring you setup the same 2 WAN ports and setup one WAN for its internet link (static, dynamic, whatever your ISP uses), and set the 2nd WAN with the setting for its link to the main gateway. Make sure you set up both WAN ports correctly - what you temporarily set in standalone wont be remembered after adoption!

Now, set up its LAN to be something different from anything on your main or remote sites this is important or the VPNs wont work
In my example, i set it to 10.255.255.0 /24 with a high VLAN ID. This LAN will not be used for anything so no DHCP is necessary

STEP 5
Connect the VPN server gateway from its second WAN to the main router WAN you configured for it, It will adopt over its dedicated WAN<>WAN link just fine with the port forwarding you enabled

You now have a WAN<>WAN link between both gateways ready for a dedicated VPN link between them!
STEP 6
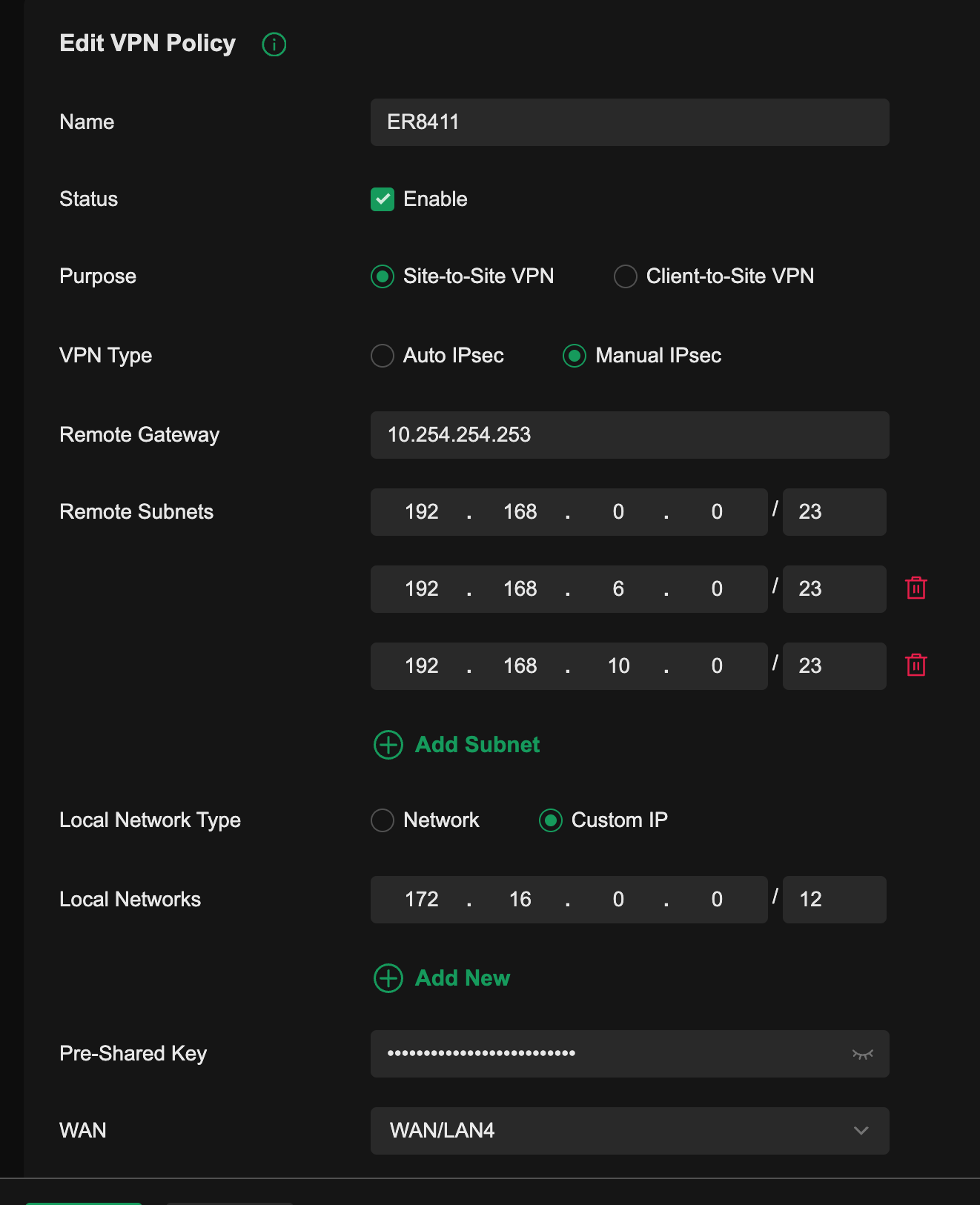
Setup the VPN link between them on both sides. This is a dedicated router to router VPN and all you need to do is include the IP ranges on the main site you wish to share to all the remote sites. You need to include the remote and dial-up IP ranges on both sides. In my case, all remote site LANs and dial-up VPN clients can fit inside the 172.16.0.0/12 subnet, so i just need to include that on both sides of the VPN.
ER8411 Side


ER7206 Side

STEP 7
The VPN between the two gateways will now establish
(from my ER7206)

At this point - congratulations! this was the hardest part! You now have a dedicated VPN server, ready to accept incoming VPNs, with its own link to your main site. You dont need any ACL rules managing anything on your main site, it will all be done here on the new VPN server gateway!
Step 8
Setup your remote site and dial-up VPNs on the new gateway
Because the new VPN server has a direct tunnel into the main gateway, you can add any of the networks it has access to over its dedicated WAN<>WAN link as "local networks" in your incoming remote and clients VPNs, just like you could as if they were set up on the main site. Rememberm you will need to change all VPNs at the other end to point to this VPN server public IP !

STEP 9
Set up the control ACLs
Now, since all VPNs are coming "in" through a wan port, you can set up ACLs on the "WAN IN" direction - either from the remote clients on the VPN servers internet facing WAN, or to control clients on the main network, its WAN IN on the dedicated WAN<>WAN port
In my case, i was able to combine them all into 3 groups to control access from any side to any side

Testing
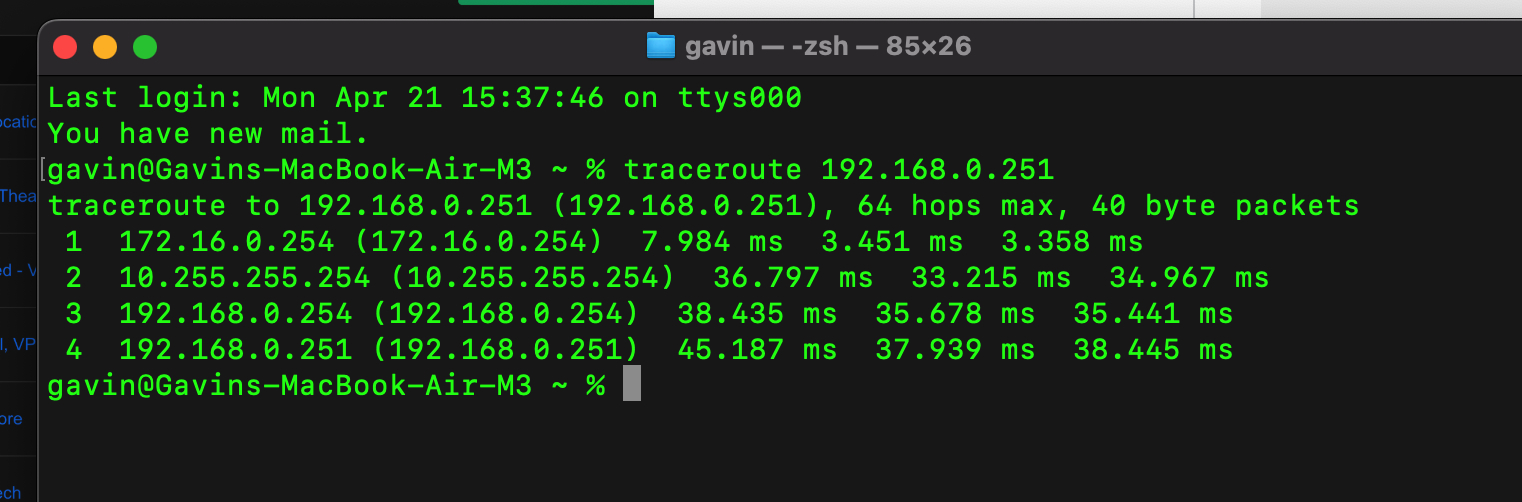
I am at home, i have a ER605 establishing VPN to the dedicated VPN server. I can traceroute to one of my network switches on main site (192.168.0.251)
On the Main site, i can traceroute to a switch at a remote site 172.22.1.253

The VPN server is correctly routing all VPN traffic in all possible directions, as allowed by its Gateway ACL rules.
