Knowledge Base Implementing Auto VLAN Blocking (Current and Future VLANs) with Switch ACL
Hello all,
Update 05/14/23 - This has been updated multiple times. Each post in this topic is an additon to the configuration of previous post. So to see the latest update/addition, refer to my last post in this thread.
Original Post:
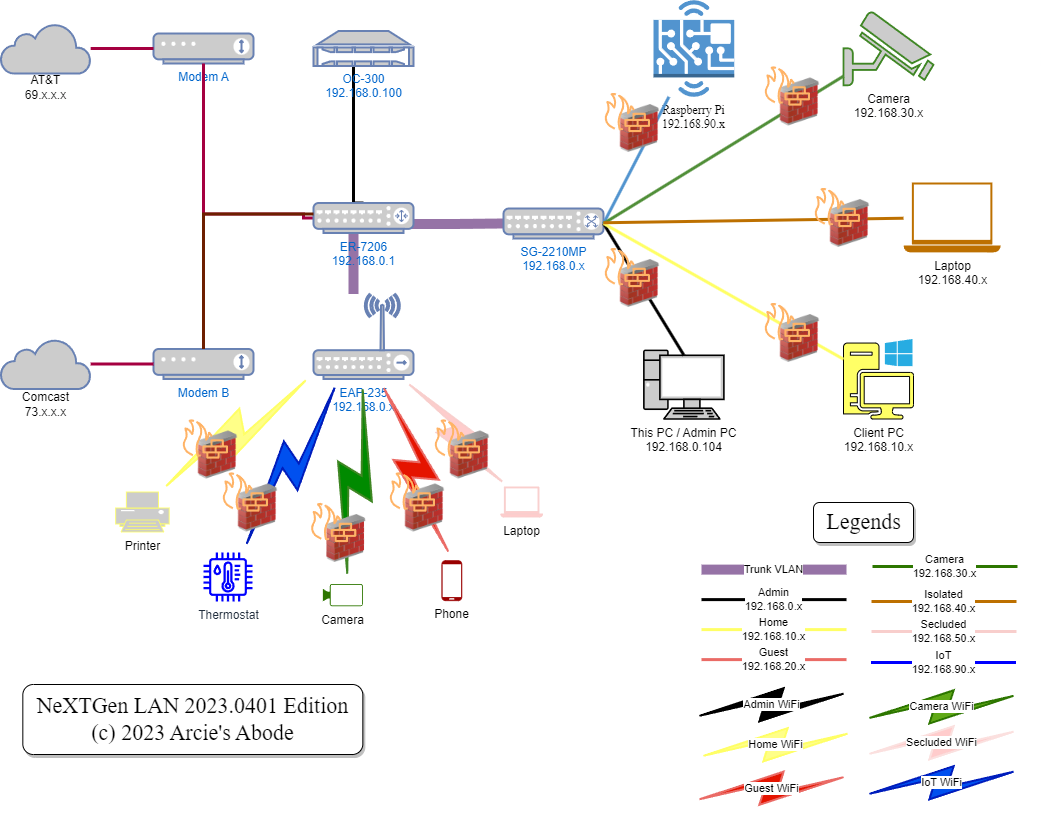
I'd like to share my old LAN Configuration that's switch-centric, I call it NeXTGen LAN. I had this config way back when I first encountered Omada ~3 years ago, I was running ER-605/SG-2210MP/EAP-115. One of my challenges back in the days, was that all VLANs can see each other by default. It's not much of an issue, except that, for the life of me, I can't figure out why my Gateway ER-605 can't do LAN ACLs In Omada Web Console. So long story short, because I spent a lot of time fiddling with ALL the options in Omada, I finally ended up putting all my ACLs on the Switches. I realized quickly that, when doing VLANs and ACLs in Omada, while the interface became familiar to me, blocking each and every new VLANs became somewhat of a chore.
Use Case:
Automatic blocking of InVLAN (same VLAN) and InterVLAN (across VLANs) traffic for current and future VLANs. The ACL config consists of two main ACLs (Lock and Key), and support ACL (Doorway). The "Key" ACL (Permit Admin VLAN) prevents lock out from the system, and allows Admin to create "Doorway" ACLs. "Doorway" ACLs are what defines a VLAN's identity. The "Lock" ACL (Deny ALL) stops everything else . This allows the Network Admin complete control of how traffic flows from one VLAN to another. You can watch my companion video here if you need more info.
ReadMe Stuff:
If you are new to Omada, I highly suggest you try the 1st and 2nd NewGen LAN before trying this out. There's also the 3rd and 4th revision (final) of NewGen that is very applicable to many types of home network. If you still would like to try this, please read the WARNING below (or hear me talk about it), and you can see ACL Configuration and Demo in Action starting in Part 3 of this video.
::WARNING::::WARNING::::WARNING::::
- A slight mistake can result in full network lockdown, getting no access to Omada, and having to factory-reset all devices.
::WARNING::::WARNING::::WARNING::::
- Key ACL must always be the FIRST ENABLED ACL
- Doorway ACLs must always be in-between Key and Lock ACLs
- Lock ACL must always be the LAST ACL. ENABLE only when Key ACL is the first ACL and Key ACL is verified to be Enabled.
::WARNING::::WARNING::::WARNING::::
Definition of Terms:
- NeXTGen LAN = Next Generation LAN (Switch-centric + EAP ACL).
- NewGen LAN = New Generation (Gateway ACL + Switch ACL + EAP ACL)
- InVLAN = Network Traffic within the same VLAN (i.e. 192.168.0.10/24 and 192.168.0.20/24)
- InterVLAN = Network Traffic across different VLANs (i.e. 192.168.0.100/24 and 192.168.100.100/24)
- Current VLAN = existing
- Future VLAN = yet-to-exist VLAN
VLAN Info:
Note that the ACLs listed below only applies to "Live" as I am still in the process of re-creating and re-validating the VLAN ACLs. As for the "Planned" ACLs, I have tested them in the NewGen Config and old firmware, but not with this configuration. I plan to amend/update as soon as I have tested them.
Live:
- VLAN 1-Admin (192.168.1.x)- this is the Native/Default VLAN 1. Granular Access to Home VLAN with VNC
- VLAN 10-Home (192.168.10.x) - Access to Internet and Neighbors Only
Planned:
- VLAN 20-Guest (192.168.20.x)- Access to Internet only, no access to same-VLAN devices. Wireless ONLY
- VLAN 30-Cameras (192.168.30.x)- Access to same-VLAN devices only, no Internet
- VLAN 40-Isolated (192.168.40.x)- Access to Internet only, no access to same-VLAN devices. Wired ONLY
- VLAN 50-Secluded (192.168.50.x)- Access to Internet only, no access to same-VLAN devices. Admin VLAN can reach Secluded clients. WiFi ONLY
- VLAN 90-IoT (192.168.90.x)- Access to same-VLAN devices with Internet, granular access to Home VLAN with DNS
- Guests WiFi and Secluded WiFi, make sure the Guest Network check box for Wifi is checked
Device List:
-
ER-7206 v1 / v1.2.3
-
OC-300 v5.7.6 / v1.14.7
-
SG-2210MP v1 / v1.0.7
-
EAP-235 v1 / v3.1.0
::WARNING::::WARNING::::WARNING::::
- A slight mistake can result in full network lockdown!
::WARNING::::WARNING::::WARNING::::
Switch ACLs:
- Permit Admin LAN (Key)
Policy: Permit
Protocols: All
Source > Network > Admin
Destination > IP Group > (Subnet 192.168.0.1/16, 172.16.0.1/12, 10.0.0.1/8)
- Permit InVLAN Home (Doorway)
Policy: Permit
Protocols: All
Source > INetwork > Home
Destination > Network > Home
- Permit Admin VNC (Doorway)
Policy: Permit
Protocols: All
Source > IP Port Group > (Subnet 192.168.10.1/24, Ports: 5800, 5900)
Destination > Network > Admin
- Deny InterVLAN (Lock)
Policy: Deny
Protocols: All
Source > IP Group > (Subnet 192.168.0.1/16, 172.16.0.1/12, 10.0.0.1/8)
Destination > IP Group > (Subnet 192.168.0.1/16, 172.16.0.1/12, 10.0.0.1/8)